Comparison of furry website HTTPS configurations
Security is necessary for one's own protection, both offline (to protect one's physical safety and possessions) and online (protecting identity, money and, as the our digital and real lives become more integrated, even physical possessions). Our own behaviours and security systems need to work together to be effective. It's no good having the latest burglar alarm, strong locks on your doors and a security gate if one leaves the door wide open. Similarly, it's great to lock the door each time one goes out - but if that door is secured solely by a latch, it won't be effective. As I've given some basic guidelines on how to stay safe online, I'm now comparing how furry sites are helping their users stay safe.
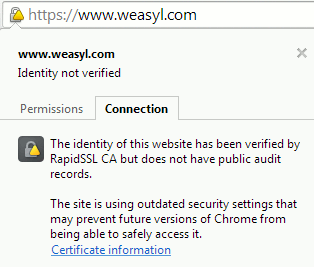
Update (Jan 28): All Weasyl servers now receive an A grade, however the server configuration is still not consistent.
One basic way of increasing security online is for websites to use HTTP Secure (HTTPS). This has two main functions. First it makes sure that one is connected to the intended website, preventing “man-in-the-middle” attacks, and, secondly, it encrypts data between end-points, preventing eavesdropping. This is essential for email and banking sites, but it's a good policy for all websites. Many furry sites use or have an HTTPS version available. HTTPS is not the only way of securing a website, and does not solve all problems, but it is a good first step.
I used the Qualys SSL Server Test, to test the SSL implementations of a variety of furry and furry-related websites. Qualys is a US-based provider of cloud security, compliance and related services. As a publicly available tool, anyone can confirm or expand on the results.
Test results
The results are shown in decreasing score, sorted by grade, whether HTTPS is forced and then by total score.
| Site | Address | Force HTTPS | Certificate | Protocol Support | Key Exchange | Cipher Strength | Grade |
| Inkbunny | https://inkbunny.net/ | Yes | 100 | 95 | 80 | 90 | A+ |
| e621 | https://e621.net/ | Yes | 100 | 95 | 90 | 90 | A |
| F-list | https://www.f-list.net/ | Yes | 100 | 95 | 90 | 90 | A |
| Flayrah | https://www.flayrah.com/ | Yes | 100 | 95 | 90 | 90 | A |
| SoFurry | https://www.sofurry.com/ | Yes | 100 | 95 | 90 | 90 | A |
| Fur Affinity | https://www.furaffinity.net/ | No | 100 | 95 | 90 | 90 | A |
| WikiFur | https://en.wikifur.com/ | No | 100 | 95 | 90 | 90 | A |
| DeviantArt | https://www.deviantart.com/ | No | 100 | 95 | 90 | 90 | B |
| Weasyl | https://www.weasyl.com/ | Yes | 100 | 0 | 80 | 90 | F |
For sites returning multiple servers the first entry was taken as representative if all received the same score. If different servers (different IP addresses) received different scores then the lowest score was taken. Weasyl and DeviantArt both return an “inconsistent server configuration” error with the lowest score shown above; for both of them the other servers receive an A rating. To test if HTTPS was forced, the HTTPS portion of the URL was replaced with HTTP and the new URL was entered in Chromium 39. If the site redirected the browser to the HTTPS version it was considered enforced.
Test details
 At first it looks odd that Inkbunny receives an A+ grade while achieving scores equal to or slightly lower than other sites. While Inkbunny would've normally received an A grade, its score was increased A+ due to supporting “HTTP Strict Transport Security with long duration.” This protects communication with Inkbunny by ensuring that server and user communicate through a secure connection, resisting attempts to force the use of insecure connections.
At first it looks odd that Inkbunny receives an A+ grade while achieving scores equal to or slightly lower than other sites. While Inkbunny would've normally received an A grade, its score was increased A+ due to supporting “HTTP Strict Transport Security with long duration.” This protects communication with Inkbunny by ensuring that server and user communicate through a secure connection, resisting attempts to force the use of insecure connections.
 Inkbunny, F-list and DeviantArt all use SHA-256 with RSA to sign their certificates. Other sites tested use the weaker SHA-1 with RSA. As SHA-1 support is intended to be discontinued in 2016, these sites will need to update their configuration to the new standard. In fact, sites with long-lasting certificates using SHA-1 may be shown as partially insecure on current browsers, as Google states:
Inkbunny, F-list and DeviantArt all use SHA-256 with RSA to sign their certificates. Other sites tested use the weaker SHA-1 with RSA. As SHA-1 support is intended to be discontinued in 2016, these sites will need to update their configuration to the new standard. In fact, sites with long-lasting certificates using SHA-1 may be shown as partially insecure on current browsers, as Google states:
That’s why Chrome will start the process of sunsetting SHA-1 (as used in certificate signatures for HTTPS) with Chrome 39 in November. HTTPS sites whose certificate chains use SHA-1 and are valid past 1 January 2017 will no longer appear to be fully trustworthy in Chrome’s user interface. [example at left]
Inkbunny also provides forward secrecy for all tested clients except for outdated software configurations (IE6 on XP, which fails the handshake completely, and IE8). Forward secrecy means that even if someone gains access to the server's private key, they will not be able to decrypt previous communications between the user and server. Weasyl gives almost the same results on those tests, but also fails the IE8 handshake. Other sites do not offer forward secrecy for as many configurations and many fail handshakes with multiple configurations.
DeviantArt was capped at a B grade for accepting the once-widely-used RC4 cipher, which has known vulnerabilities. There were no other major problems detected for DeviantArt; if it didn't accept RC4, it would've received an A grade.

F-List received an A grade, but only works in browsers with SNI support. For the most part that will only affect users on outdated systems, for example using Windows XP, IE6 or lower, or the Android 2.x browser.
Weasyl suffers greatly in this test due to just one server with a different configuration to the others. The server in question is vulnerable to OpenSSL CCS vulnerability (CVE-2014-0224), resulting in the score being capped at an F rating. This result is unusual as the Weasyl server settings were otherwise good. Despite using SHA-1, Weasyl enforces HTTPS connections and supports HTTP Strict Transport Security on some of its servers. In addition, this deviation was not present a few weeks ago.
Discussion
It's pleasing to see that many furry sites offer good security options, with many doing better than their more-professional competitor, DeviantArt. Inkbunny offers the highest security out of the tested sites due to extra security features, a superior signature algorithm and enforcing HTTPS connections. It is unfortunate that many of the sites do not enforce HTTPS connections when they have the opportunity, going against the recommended best practices. Fur Affinity generally uses an insecure connection with the exception of the login page.
Another security flaw on some furry sites is the failure to secure the entirety of a webpage. When fragments of a page, such as images, are insecure, it undermines the whole system - attacks can often be launched through those elements to compromise the secure channels. While Flayrah is generally secure, the front page contains unencrypted elements, as do SoFurry user pages which embed external images (example).
At other times sites have taken actions which do not seem to have considered user security. For example, in a recent DDoS attack, SoFurry disabled HTTPS (see here and here). While this had the positive effect of keeping the site up and functioning, it also meant disabling security when it might most be needed. An attacker could take advantage of this vulnerability to subject SoFurry users to a more serious attack.
When asked about this, SoFurry administrator Toumal maintained that the possibility was small:
So I made the call to just support http during these attacks. Because everything else would not have been practical. It doesn't mean "disabling security", it means that encryption was not available. Encryption does not equal security. So yes, while someone might use a DDoS to force us to drop encryption, that's kind of a far fetched scenario. They can just use sslstrip or other attacks, or go for the endpoint itself (i.e. the user's computer) - which in most cases is a MUCH easier target
However he did say he could tell users to consider the implications of using a plain HTTP connection during an attack and did do so during a subsequent DDoS. This is now largely irrelevant as, since Saturday, SoFurry has been reconfigured to enforce HTTPS across the whole site.
HTTPS is enforced for six of the sites tested. However, major sites such as Fur Affinity and DeviantArt do not do this. How can users enable encryption? In some cases, you can manually enter the 'https:' (or change your bookmark to it). If the site is appropriately configured, all navigation will remain in the secure version once you've connected to it. This won't happen if you click on an HTTP link while browsing, though; and DeviantArt will switch you back straight away. Plus, some sites may still use HTTP behind the scenes.
A better option is to install the Electronic Frontier Foundation's (EFF) HTTPS Everywhere – a browser extension that automatically converts URLs to a secure version according to a set of rules. Although it does not support the above sites by default, the HTTPS Everywhere Atlas has rules for the above sites that do not enforce HTTPS connections. There is partial support for Fur Affinity but, currently, the DeviantArt ruleset is disabled with the note, “site operator says not ready yet.”
There are notes of caution regarding these results. HTTPS does not provide perfect security; for some attacks it doesn't provide any protection. It is one small aspect of online security, and care should be taken not to give the results more meaning than they deserve.
In addition, due to the rapidly changing nature of the internet, these results are only valid at the time the tests were performed. Between the first test and the final version, many sites made changes and scores have, in some cases, changed dramatically. Originally SoFurry received a C grade, although that was dealt with in minutes when the results were brought up with Toumal; it only recently began forcing HTTPS connections. F-list increased its score from a B to an A during the writing of this article, while Weasyl dropped from an A to an F due to poor configuration of a single server. An attempt was made to contact the Weasyl administration, but no reply had been received by the time this article was submitted.
Conclusion
The large-scale DDoS attack that hit many furry sites a few months ago and the chlorine attack at MFF should have made furs more aware of the need for awareness and security. While not addressing either incident specifically, HTTPS is a basic security step (see the Chromium project's proposal to mark HTTP sites as insecure) that's available to the major furry sites. Inkbunny, SoFurry and Weasyl now all force secure connections, while Fur Affinity and DeviantArt do not.
The results and linked best practice guidelines here will hopefully serve to motivate and guide site owners in improving their security. For most, the step is to enforce HTTPS for all communication with the site; for some, more drastic changes are necessary to offer a secure experience.
Flayrah, WikiFur and Inkbunny are led by GreenReaper.

About the author
Rakuen Growlithe — read stories — contact (login required)a scientist and Growlithe, interested in science, writing, pokemon and gaming
I'm a South African fur, originally from Cape Town, who spends most of his time in Europe. I'm interested in all sorts of things, particularly science, furry and some naughtier things too!
Comments
Qualys offers a useful tool, but it isn't the last word in HTTPS. There's always a new standard. For example, Inkbunny is on the HSTS preload list, which gets around having to connect to a server for HTTP Strict Transport Security to be enabled.
Of course, there's a down-side to being on the leading edge - increased security can mean tradeoffs in usability. Yesterday I got a complaint that Inkbunny couldn't be accessed on a Nintendo 3DS (probably requires SHA-1 or SSL v3). As noted above, some other sites won't work on Windows XP's IE 8, which is still quite popular in some areas.
The latest thing is Public Key Pinning, which allows you to say "only this set of public keys can sign my certificate". Forged certificates will be refused by compliant browsers, even if signed by a trusted root. I've played with it but I'm cagey about implementing it due to the risk of unintentional denial of service. (Also, if someone has the resources to forge a valid certificate for Inkbunny, we have bigger problems.)
I reached out to Weasyl about SHA-1 issue via their sysop address late last month, but didn't get a reply. Maybe it's not being monitored?
As for deviantART and FA, I started pointing Inkbunny users to their HTTPS versions about a month ago, even if they're not "officially ready".
Flayrah's front page displays images from In-Fur-Nation. This does give away the fact that you're visiting our front page, as it passes the referrer in the request. In theory it could've been used to insert content that attacked your browser (one reason it's important to keep your browser up-to-date). This is hard to fix perfectly because In-Fur-Nation is not available over HTTPS; I've set it to bounce via Flayrah for now.
Mixed-domain content can be a more serious issue if you have not taken precautions to keep your own cookies secure; your login session may be transmitted in the clear, potentially giving attackers the ability to act as you.
CloudFlare has been adopted by many sites in this list. It can certainly be better than nothing at all, when it comes to edge protection, where many attacks occur. But it is, by its very nature, a man in the middle. There are severe privacy implications. It also doesn't give users an accurate impression of what the encryption situation is behind CloudFlare (it supports HTTP backends, and can hide issues like Weasyl's).
The key is defense in depth. Do you lock sessions to IP addresses? Can you login to administrative server accounts from anywhere, if you know the right username and password? What about on-site staff accounts? How stringent are your password policies, and how are they hashed and stored in your database? Should you keep other content encrypted inside the database, in case it is compromised? Etc.
Lastly, you have to take care selecting your staff. Technological measures may be useless if they are compromised from within.
"The large-scale DDoS attack that hit many furry sites a few months ago and the chlorine attack at MFF should have made furs more aware of the need for awareness and security."
This is quite right. But there is one more aspect of security which is often overlooked: privacy.
I am going to talk about Tor. Allow me to explain how this is relevant.
Outside of the internet, I am still in the closet about furry. This is common. Until around 2005, we feared ridicule and rejection.
Then 4chan and ED came along. The stakes had been raised. Now some of us were genuinely worried about their safety. Several furries were made unemployable after slander against them on ED.
This was bad enough. But just as we were letting our guard down again, MFF 2014 happened.
MFF was a complete game-changer. Someone out there has just demonstrated they are willing to take their hatred beyond the internet. The danger isn't speculative any more.
Furries have every right to respond to this risk in different ways. For some, they will continue as normal. Openly furry. For others, it has driven home the importance of insulation. Keeping our furry lives separated from our "real" lives.
When it comes to the internet, it is easy to track people. If you are determined, it is possible to trace a person back to their legal identity. If you are an employer, you know exactly what your employees are doing on your network. This is not the place to discuss this in detail. For background, read up on the following: Panopticlick, TCP fingerprinting, unintentional identity linkage, and filing of false DMCA claims to uncover an identity.
Will someone come knocking on your door in the middle of the night? Someone who "objected" to that piece of art you posted last week? That's a lot more likely than someone killing thousands of furries at a convention. And that almost happened.
I am not comfortable with the risk.
There is one way to nearly guarantee safety: Tor.
In addition to protecting your identity, Tor provides an optional mechanism far more secure than HTTPS + certificates. Hidden services. They are no longer the preserve of drug markets. Even Facebook have one now.
But there is one small problem. Some sites actively discriminate against Tor users. Furaffinity comes to mind immediately. Other sites, like Flayrah, inconvenience the user. A difficult captcha is required to access the site. Unlike Furaffinity this is the fault of Cloudflare, not Flayrah.
Now what if you do have something to hide? If like me, you have tried to seek support in the fandom to prevent suicide? This is something which nobody should ever have linked to their real identity. Yet most furry IRC servers take extreme measures to block Tor users.
It is time to clear up the misconception that anonymous equals dangerous. There is a wealth of documented evidence disproving this link. Consider some of the more problematic individuals in the furry fandom: the vast majority have revealed their full identities online.
Anonymous doesn't have to equal spam either. The vast majority of sites quite happily accept Tor users without a spam problem. There are other countermeasures besides blocking massive IP ranges.
So to the real substance of this post: I would like to see another column added to the site summary. Where does a given site stand on their Tor policy?
A+: No restrictions at all.
A: Proof of work algorithm, or easy captchas required when registering, or posting anonymously.
B: Difficult captchas required when registering or posting anonymously.
C: Captchas required for viewing the site. Cloudflare or otherwise.
C-: Restricts Tor users to posting under a registered and approved account (which can be set up using Tor)
D: Does not allow Tor users to post at all, or requires them to bypass Tor to sign up.
F: Actively blocks Tor users from even viewing the site. Fail, no retake.
At the time of writing, Flayrah gets a C. Furaffinity gets an F for actively attempting to block Tor, even although they haven't identified every Tor exit node.
Now, I need to submit this post. Wish me luck. My eyesight is bad enough without having to squint at unreadable captchas for half an hour!
Tor and other open proxies are often used to undermine a system of site governance. Spam is just one concern; more generally, it's those who do "bad things", get blocked, and come back on Tor to do them again that are the problem.
Put simply, if you come into someone's house or place of business with a mask on, it is not unreasonable for the owner to suspect you have something to hide, and that it may be to the detriment of themselves or other guests. This is not a misconception, even if it may not be true in your particular situation: it is based on the general population of proxy-users.
Often what people are looking for is evidence of committed identity. For example, by registering an account, you may avoid captchas. Sites accept unique masks if consistently used, because they avoid the types of abuse which anti-proxy policies are designed to mitigate. Conversely, if you prevent sites from tracking you, they will naturally treat you as any other faceless stranger potentially bent on abuse.
I'm generally fine with a pseudonymous compromise but the guilty until proved innocence assumption that accompanies tools like TOR is a bit problematic. There's this example from Spain where some people have been held in jail instead of being released because they used an email service with "extreme security measures." https://www.eff.org/deeplinks/2015/01/security-not-crime-unless-youre-anarchist The example of a similar real life activity is interesting but not a perfect analogy. With the ease of online tracking it's more like someone wanting to wear a mask because someone otherwise is following them everywhere they go all day and writing it down, that would be concerning for a person.
"If all mankind minus one, were of one opinion, and only one person were of the contrary opinion, mankind would be no more justified in silencing that one person, than he, if he had the power, would be justified in silencing mankind."
~John Stuart Mill~
Many people that use Tor desire to hide something, but not necessarily from the service they're attempting to access. Sometimes you don't want your ISP or network manager to know you're accessing furry sites. Sometimes they'll attempt to actively block you from using them - many furry sites are included in "adult" blocklists, and I think FA's CDN is currently blocked in the entierty of Russia. I haven't actually checked, but it wouldn't surprise me if FA and other furry sites were blocked in otger countries with a tendency to prohibit "immoral" webpages. Anonymity isn't just about hiding from your destination.
I don't see any potential harm in at least allowing Tor users a "read only" mode. My ideal solution though would be to allow signups with some restrictions, such as requiring any content (media, commemts, journals, ect) submitted to be manually approved until a user can prove they're around for more than trolling. I know it wouldn't stop a dedicated troll, but it'd at least be enough to make most of them frusturated enough to give up.
Freakin' furrys are [nerds]way to good at all this internet stuff[/nerds]
Says the guy who just reviewed a game's mechanics without going into the freaking amazing character art.
Fair enough.
Speaking of security. Coming into flayrah via http:// now causes a redirect to a shady download manager popup site.
Probably should get into looking into why that is...
Umm, are you sure you're typing that correctly, and it's not autocorrected? It works fine here.
Of course, since it's HTTP, anyone along the connection can mess with it. (That's where HSTS comes in.)
I was incorrect, it had nothing to do with the http or https, it is in fact an advertiser and it was just random happenstance. I've been running into this issue when
An advertisement for Open Download manager hostilely takes over the entire website. I have now put in my ad blocker and will not remove it until they are removed from the ad cycle. If I want to close their window I basically crash out of my browser because it does that "Are you sure you want to close" things. I do not trust any site that I cannot close out of immediately by clicking the X button on the window.
If someone wants to test this, go ahead and remove the ad blocker you have on for Flayrah, and you'll eventually see what I mean.
I attempted to use the "Contact Us" item on that site, but clearly it wasn't made to work, just look pretty so I'll just leave me statement to them here:
Dear Open Download Manager software (848 N. Rainbow Blvd. Suite 3671, Las Vegas NV 89107),
I do not appreciate your methodology of advertising. I am trying to load a website I visit on a regular basis and it seems that you were added to their ad cycle. You somehow scripted it so that your ad will take over the entire page and I can't close without a confirmation screen asking me if I'm sure I want to leave.
Yes, I'm sure I never wanted to be on your page to begin with. Are you sure you want to keep sending me to this page and condescendingly asking if I want to leave a place you forced me to in the first place?
I have copied your address, and I assure you you have one week to stop this harassing advertisement campaign. If you do not I will be contacting the Better Business Bureau and will make sure everyone knows about your shady advertising practices. And if you can't trust a company like yours to advertise in a fair manner, then why should they trust you when it comes to software? Hell why would they want to install software from programmers who clearly act condescendingly to the computer's user?
X means CLOSE, assholes. Not ask if that's what I meant. Yes, I know what the X is meant to close the screen, do you?
Yours Truly,
Nanna Urdambisness
I think you may be wasting your time contacting them. As for Flayrah, I cannot reproduce your report.
Open Download Manager is a commonly-installed piece of malware and the information you provided to me separately suggests that another group is distributing ads for it. This is something which might easily be done by a malicious extension/plugin or a separate program running on your computer.
Other than it only happens on Flayrah's home page, and only when I have the adblocker turned off on it...
Yes, other than that. For example, you might have something which randomly opens a window every few web accesses, and since our front page has a chat widget for Newsbytes, it triggers regularly. If someone else reported this happening, I'd have more confidence that it is related to our ads, and not your computer.
I am reporting this issue to Google, in case they are able to do anything to confim or deny it on their side; for example, check the ads that have been showing on Flayrah. Unfortunately they are customized so it may be tricky to narrow it down to a set to check, but maybe they can look it up based on email address.
Prehaps the next time I'm in a writer's guild session I will turn off the ad blocker and see what happens. Though I do have ad blocker off on FA and it hasn't happened there yet.
For now I will disable that ad block. It literally is not worth all the hassle, and who likes Flash anyway?
Text ads are a more efficient use of bandwidth, in any case. :-)
This kind of extra security seen by furry sites is merely a form of "survival of the fittest". While nowadays it's quite rare, back in time you could hear stories of websites "hacked beyond repair". Since we are nonetheless target of trolls and hacker, specially from 4chan and SomethingAwful, furry sites NEED to be better than average. The irony is that those who hate us only provides us improvement in the long term. What doesn't kill us makes us stronger.
While some security measurements are nice, they always have drawbacks. Like tor. While an website supporting tor is nice, you can't just use it for absolutely everything in your life. Tor itself has vulnerabilities, and some includes a compromised tor server. In other words, doesn't matter if you have a vault-like door if the window is open. Another problem, that Tor itself is in the worst scenario, but applies to most security measurements, is that it increases the data processed and transfered. The server needs to do more stuff to encrypt and the result is a larger data, consuming more bandwidth. This also increses the costs of keeping the server.
Not to mention that there's the part of being capable of correctly installing, configuring and using such security measurements. Some aren't that easy. Sometimes, they're great, but if unproperly configured it might make the server even MORE unsafe, not to mention that it would also be giving a false impression of security.
For internet safety beyond furry sites, the internet per se is very safe and private, but people often choose the least safe places to go. Even though some sites can be compromised, it's against their will. However, there's always legal base to use against those who failed in providing security and privacy. Unless you agree that you actually don't give a fuck about your security and privacy. And you agree that by adhering to the site's ToS and PP. Facebook and most google's sites have atrocious ToS and PP, with some aspects sharing characteristics of malwares and spywares even. And even when they can be fairly private by changing certain configurations, they're usually 100% not private by default.
If you're a closeted furry and NEED privacy, it's gonna be pretty tough to succesfully hide it, but whatever you do over the internet to hide that, is something you should be doing closeted or not, furry or not.
Post new comment